
If you want to pursue a job in cybersecurity or a hacking-based company? In that case, you’ll need to be familiar with hacking tools and terminology to secure the system from malicious hackers. Hacking has evolved into a professional discipline in today’s digital world because every firm strives to secure its system and data from illegal system breachers.
To learn more about Ethical hacking and how to hack emails, you can join the Ethical Hacking course Online and get a comprehensive understanding of types of hackers, email hacking, and cybersecurity.
Every organization, including government sectors, assign ethical hackers, and these hackers have the authority to penetrate the system. Ethical hackers are also in charge of penetration testing to improve the system’s security.
Almost every firm needs ethical hackers to assess the system’s vulnerabilities. Authorized hackers with the authority to analyze the system are ethical hackers. Ethical and illegal hackers utilize the same techniques to break into a system, but White Hat hackers have the authority to do so, and their goal is to improve security. On the other hand, Malicious hackers use the system to steal data from businesses.
So to have a better understanding of types of hackers, hacking tools, technics, and their terminologies, Ethical Hacking Course in Chennai will help you understand more about the legal and illegal aspects of ethical hacking and email hacker tools.
Now, we shall discuss how to hack emails and how email hacker uses email hacking tools and techniques. Email hacking utilizes three following steps:
- Email spoofing
- Social engineering tools, or
- Deploying viruses in a user system.
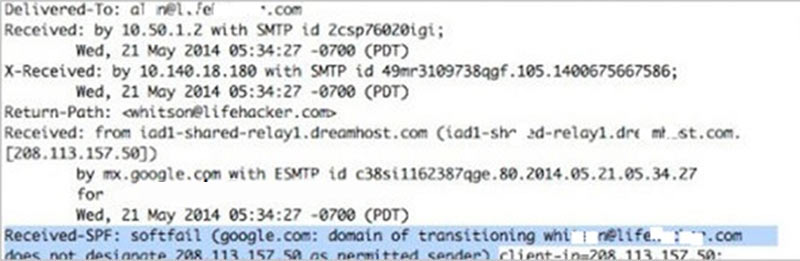
Email Spoofing
In email spoofing, the junk mail is sent from a familiar username so that the receiver of the mail assumes that he is familiar with that person and opens the email. In such cases, the hackers send the pessimistic links, content, claims to transfer money, bank details, etc.
Social Engineering
Phishing emails generate marketing emails to various people, claiming significant discounts in exchange for collecting the personal information of someone. In Kali, you have tools to tricks and tips that can hijack an email.
Phishing tactics can also be used to hack into email accounts. Take a look at the image below.
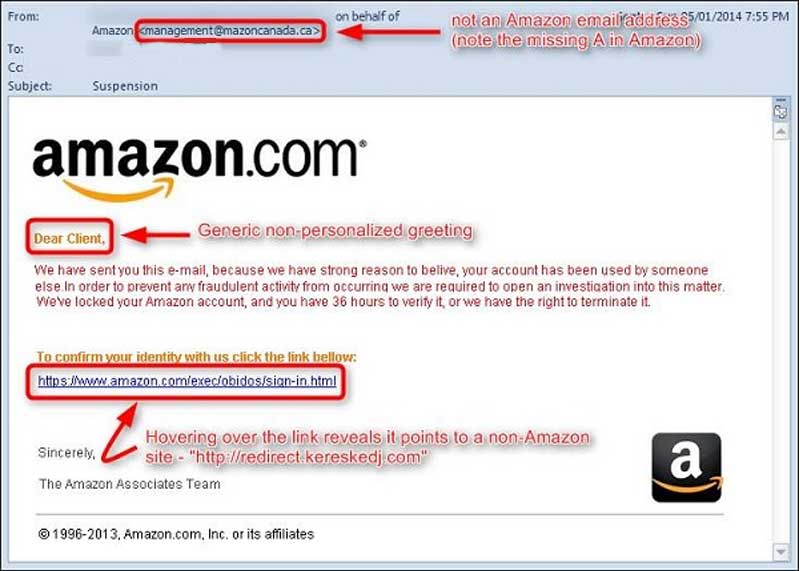
The spam email link may automatically deploy in the user’s system, divert the authorized user into a malicious website and track their complete details such as user code, account numbers, financial details, card PIN, etc.
Illegal hackers utilize phishing attacks, and this method is effortless to redirect the authorized user. Further, it is easy to breach the system and access the confidential data of an individual and organization.
Installing Viruses in a User SystemThe foremost technique used to hijack your email user ID is deploying the virus into your system. Once you click the link, the hackers steal all your data or contaminate your email by installing malware into your computer. And with the aid of deployed viruses, hackers try to hack your password and user ID.
How can you know if your email account has been hacked?
Spam email targets several people you know.- When you try to log into your email, the password is no longer valid.
- When you click on the “Forgot Password” button, it does not take you to the intended email address.
- You have a lot of spam in your Sent Documents category that you aren’t aware of sending.
Tips to protect your email hijacking:
If you suspect that your email has been hacked, you should take the following steps:
- Change your passcode and user name as soon as possible
- Report your friends not to open the mail that they receive from your mail ID
- Report authorities that your account has been hacked
- Update a reliable antivirus program on your computer.
- If it’s possible, set it up DOUBLE authentication passwords.
By this, you would have understood how to protect your Email from Hijacking and know if your email account has been hacked. So to learn terminologies and tools used by ethical hackers and protect your system from malicious hackers. If you are interested in cybersecurity, you can take an Ethical hacking course and equip yourself with the necessary knowledge.