
Half of the war ends when you find your target. Once you fix your target, there are different ways to hack the network or system.
In this blog, we shall discuss types of scanning in ethical hacking, which of the following is not a type of scanning, and what are the types of scanning.
At the end of this blog, you will understand how to gather precise information about your target by utilizing Network Scanning for Ethical Hacking.
If you are interested in Ethical Hacking or Cybersecurity, you can join the Ethical Hacking Online Course, which will help you understand network scanning techniques, scanning and enumeration in ethical hacking, and many more.
What is scanning?
- Scanning is a set of methods for finding the host, ports, services, OS, and architecture of the target system to find the weaknesses of the live port. The primary aim of the hacker is to find the network’s vulnerabilities and threats.
- Scanning is gathering more data through active and aggressive reconnaissance methods.
- Networking scanning is the process of evaluating the active hosts, services and ports.
- The primary goal of identifying these activities is to target application uses.
- The point in the system aids the ethical hackers in finding the vulnerabilities in the system, and through these weaknesses, hackers can breach the network or system.
- The primary aim of the Network scanning for the white hats is to find the security hole and protect the network from the Black Hat Hacker.
What are the types of scanning?
Scanning can be categorized into three types:
- Network Scanning
- Port Scanning
- Vulnerability Scanning
In this blog, we shall look at networking scanning in detail.
Network Scanning
- Network scanning is used to analyze the target organization.
- The primary aim of Network Scanning:
- Understand the live hosts, Internet Protocol address, and open ports of the target system or network.
- To become accustomed to the services offered by the host computer
- To evaluate the Operating System and system architecture of the target system
- To discover and deal with exposures in the Live System.
Scanning Methodologies
- At first, hackers or pen testers will analyze the live host.
- Check Transmission Control Protocol or User Datagram Protocol number.
- Scanning beyond Intrusion Detection System
- Banner Grabbing
- Banner Grabbing is obtaining data about the target network, system, or services that run on its open port.
- The primary tools used to carry out a Banner-grabbing attack are Telnet and ID Serve.
- Hackers and criminal intent may use this information to demonstrate lists of appropriate exploits.
- Scanning is to find the vulnerability
- Prepare Proxies
For example, if you are an ethical hacker and intend to find out the vulnerabilities in the network or system, you can attempt to target if you find systematic vulnerabilities.
In such a case, an ethical hacker can utilize network scanning to find vulnerable points in the system. A network is scanned for ethical hacking to identify these weak places in the system that a Black Hat Hacker can exploit to attack the network. Then, the corresponding teams focus on enhancing the network’s security.
To learn more about ethical hacking, you can join Ethical Hacking Course in Chennai, which will help you understand the scanning methodology, types of networking scanning and objective of network scanning in ethical hacking.
Which of the following is not a type of scanning?
Among various types of scanning like network scanning, port scanning, and vulnerability scanning, Cloud Scan is the one which is not included in the port scanning.
How is Network Scanning different from Reconnaissance?
As we already discussed, network scanning is the process of finding security points. To make you clear, we will discuss an example for network scanners:
Assume that the army administrator and crew members will plan to attack the enemy lair after finding out the location and information about the beginning state the analyze the way to reach the liar. So, using Reconnaissance, you have gathered all information. Now is the time to find the point through which you can attack the liar or enter the terrorist liar to attack the enemy. This same process is utilized in the network breach.
You would have gained a basic understanding of Reconnaissance from the above example. Surveillance is the process of collecting information about the target system. By adopting this method, we can gather all possible vulnerabilities in the system or network. Networking scanning can be categorized into various types based on the scan recognizer.
What are the types of scanning for Ethical Hacking
Though there are various types of scanning utilized by ethical hackers, the two main scanning methods are utilized for finding vulnerabilities in the system.
- Port Scanning
- Vulnerability Scanning
Port Scanning
As the name implies, Port scanning is used to find active ports on the internet or network. In this type of hacking, the port scanner will transmit the client request to the active ports on the network. The active port which sends the resp[oce massage, the port scanner will save the entire details about the ports that accept its request. By this method, active ports are found.
There are various types of Port Scanning. Below is a list of some of the most used ones:
- Transmission Control Protocol scanning
- synchronization scanning
- User Datagram Protocol scanning
- ACK scanning
- Window scanning
- FIN scanning
Vulnerability Scanning
It is a common network scanning methodology utilized by ethical hackers. Hacking is the technique the hacker utilizes to find vulnerabilities in the system or network. In this type of scanning, the hacker can identify the weakness due to less security configuration.
Now, you would understand the essential concepts of ethical hacking like:
- What are the types of scanning?
- What is scanning in ethical hacking?
Now, we shall discuss some important tools and how to use them in network scanning.
How to use Network Scanning tools?
The main purpose of utilizing network scanning is to control, manage, and maintain, assure the system using data located by the scanner. Network scanning is employed to identify available network services, find and identify any filtering systems in location, look at what OS are in use, and protect the network from a malicious hacker.
Now, we shall use the Kali Linux operating system, which has built-in features and hacking tools. As a first step, your system should be updated with Kali Linux. If you have not yet installed Kali Linux, you must configure it in your system.
Join Ethical Hacking Course In Bangalore, which meticulously designed the course syllabus for Bangalore-based students to learn from their comfort zone.
Nmap for Network Scanning
Nmap is a free and open-source network scanner. With the aid of this Nmap, you can scan the network by Internet protocol addresses of the target system or network.
- $ nmap 1.2.3.4
- Or by the hostname
- $ Nmap domainname.com
Before scanning a network, you must analyze whether you have authorization for scanning. Without authorization for hacking, the activities come under illegal attack. So, get prior authorization from the organization.
Moreover, while scanning, don’t ever choose the random network. Hackers must understand that without having permission to hack, one cannot learn about Nmap. So, if you are interested in practising scanning, you can visit scanme.nmap.org, which the Nmap organization provides.
Let’s try scanning this. Open a terminal in your system and run the below command:
- $ nmap -v -A scanme.nmap.org
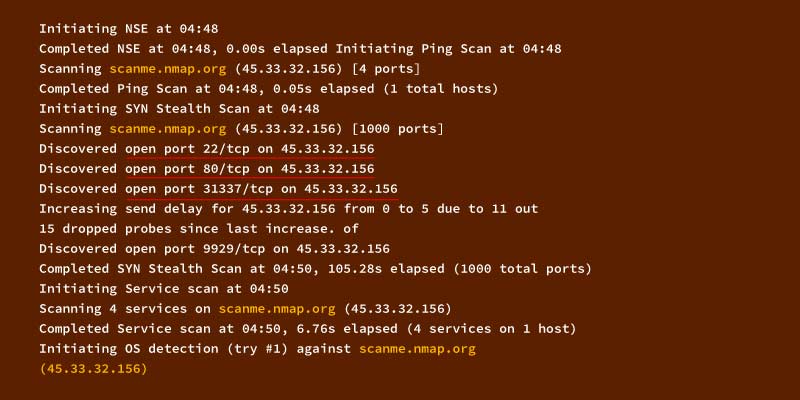
Now, as a result, you would have understood the open ports displayed by the network. The command mentioned above has the options:
- ‘v ‘is for verbose output
- ‘A ‘is to detect the Operating System.
Many options are utilized with the Nmap tool to obtain distinct sorts of results.
Nikto for Network Scanning
Nikto is primarily utilized for scanning a web server. Using this scanner, we can evaluate the risky files and legacy systems. So, with the help of this scanner, we can hack by breaching the network. Moreover, with the aid of this Nikon scanner, we can scan the web server within a limited time.
To employ Nikto, open the terminal and run the following command:
- $ nikto -host scanme.nmap.org
You should see a similar output.
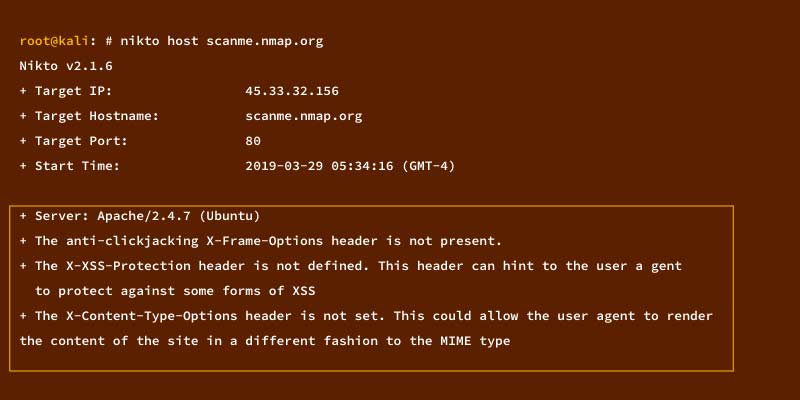
From the above image, you should have understood how the result presented by Nikto. These results aid in understanding the network’s weaknesses or applications being scanned. Once you discover the network’s defect, you can select appropriate attacks to hack the network.
Nessus for Network Scanning
Nessus is a powerful vulnerability scanner. In Kali Linux, this scanner is not installed by default. So, let me show you how to install it first.
Open a browser and visit www.tenable.com/downloads/nessus and click “Get Activation Code “.

There are two versions of Nessus: Nessus Essentials. Nessus Professional and Tenable.io. We shall use the free version, so click on the “Register Now” button under “Nessus Home “.

On the next page, you can enter your name( first and last) and Email Id. After entering your name and email ID, the link will be sent to you, redirecting you to download the page.
Download the appropriate file. Since the version of Kali Linux is compatible with the AMD64 model, you can download the .deb file for that architecture.
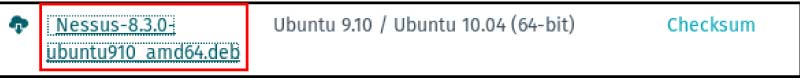
After the download has been done, open the terminal and run the following command to deploy Nessus:
- $ cd Downloads
- $ dpkg -i Nessus-8.3.0-ubuntu910_amd64.deb
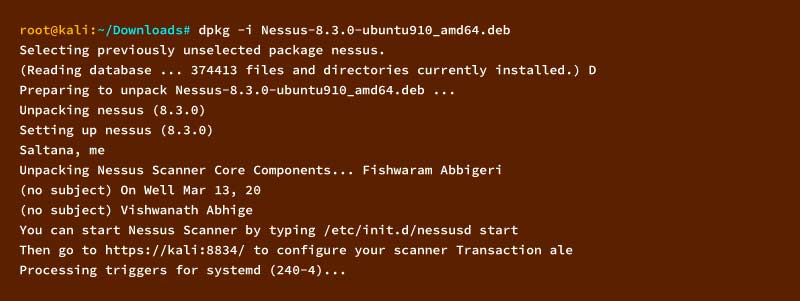
Now, after its installation, you can start using the Nessue service. Look at the below command:
- $ /etc/init.d/nessusd start
After the service gets started, open an internet browser and head to //kali:8834/

Now, you can enter your passcode and username ID. You can enter the activation password already sent to your email on the next page. After successful completion of activation, Nessus will take some for downloading the required Plugins. Once the configuration got over, you will get like this:

Click “New Scan” in the top-right corner to scan a network. On the next page, Nessus provides various types of scanners. You can choose the Basic Network Scan.

Click “Save” after entering the target, directory, description, and name of your scan.
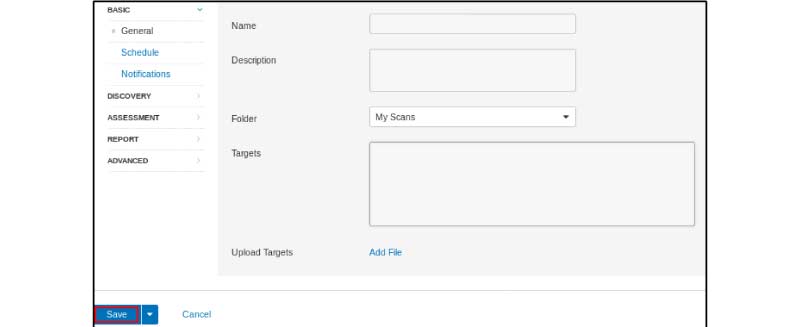
Next, Click the ‘start’ icon after selecting the scan.

Once the scanning process got over, you can notice the vulnerability result under the “Vulnerabilities” tab.
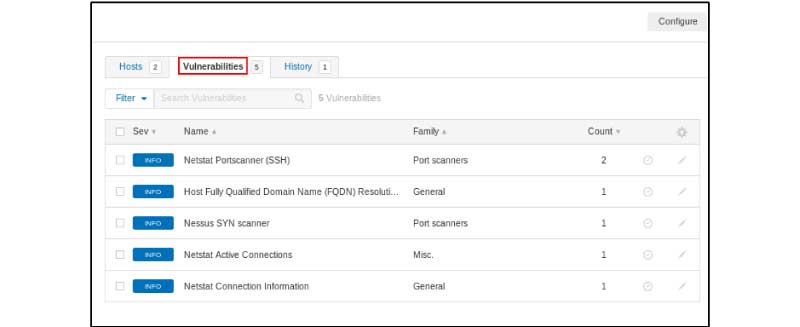
The scan results display the data and vulnerabilities discovered.
Nessus can be utilized in this way for network scanning during ethical hacking.
Once you have gathered the complete details about the target, it will be more comfortable to test for vulnerabilities. Moreover, example for network scanner are:
- Acunetix
- OpenVAS
- Intruder
- Wireshark
- Core Impact
- Skyboxsecurity
- Retina
So, utilizing these tools for network scanning will help you scan the target system or network easily.
Now, you would understand the example for network scanner, what are the types of scanning, which of the following is not a type of scanning and the types of scanning in ethical hacking.
So, if you want to learn more about ethical hacking techniques and strategies, you can join Ethical Hacking Course in Coimbatore, which will help you learn the core concepts of ethical hacking and aid you in mastering the techniques of ethical hacking.